Introduction & Requirements
Detecting phishing and malware incidents managed by Zero-hour Auto Purge (ZAP) to summarizing crucial event data for insightful analysis, we’ll explore a targeted KQL query designed to enhance your organization’s security posture. Whether you’re an IT professional, a security analyst, or just keen on cybersecurity practices, understanding how to utilize KQL for email security can be a game-changer in your defensive arsenal.
Purpose & Requirements
- Security Analysis: This query is useful for security analysts looking to review incidents of phishing and malware that were detected and acted upon by ZAP after initial delivery.
- Incident Response: The summarized information can aid in incident response activities, offering insights into the scope and specifics of email-based threats.
- Compliance and Reporting: For organizations needing to document or audit their responses to potential email threats, this query provides a structured way to gather necessary data.
- Requirements: 365 XDR defender & Sentinel if possible
- Azure Subscription and creation of a. dashboard
Dashboard objectives
- 24 h Phish and zap Malware Items
- Dashboard link can be used and pinned in a Sentinel alerts
creating the dashboard
- Create the dashboard in azure and set appropriate permissions using the following query
EmailPostDeliveryEvents
| where ActionType == "Phish ZAP" or ActionType == "Malware ZAP"
| join kind=inner (
EmailEvents
) on NetworkMessageId
| summarize by
ReprocessTime = TimeGenerated,
OriginalDeliveryTime = TimeGenerated1, // Ensure 'TimeGenerated1' is defined in 'EmailEvents'
SenderFromAddress,
Subject,
ActionType,
DeliveryLocation,
RecipientEmailAddress,
OriginalDeliveryLocation = DeliveryLocation1 // Ensure 'DeliveryLocation1' is defined in 'EmailEvents'
Dashboard looks
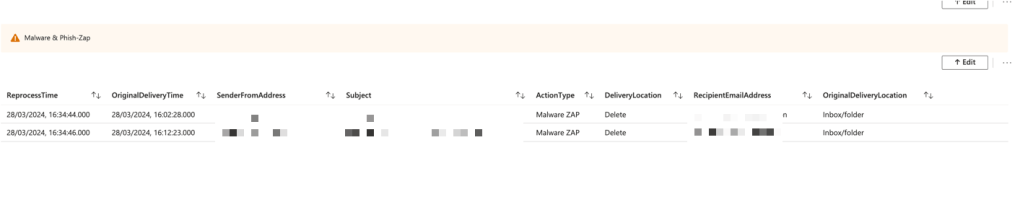
Quickly Overview all zapped/Malware items based on time and on demand at any time