Introduction
Detecting tainted accounts in Active Directory (AD) that allow users to use a blank password is a significant security concern. This kind of configuration can severely compromise security by providing an easy entry point for unauthorized users in legacy systems ( Active directory). not needing a password to login.
This is not a default behaviour and requires altering specific attributes in the user account control settings. This alteration is typically restricted to IT administrators or users with equivalent privileges.
Those accounts as per MS documentation would not have blank passwords in azure ad , however it is highly recommendable avoiding, detecting and remediating if found
Example of db user with the parameter set in Active Directory
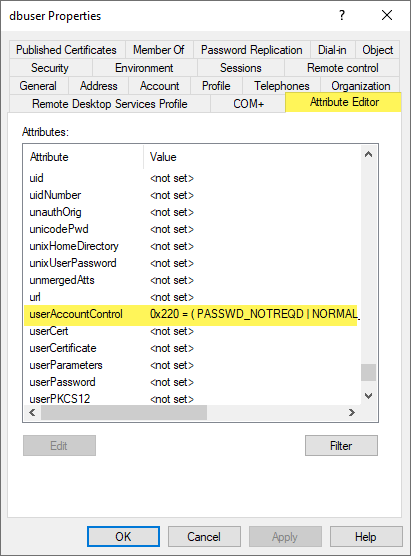
Example scenarios
- IT members that no longer work in the company made changes to users or service accounts ( Former IT members )
- Insider threat or shadow IT : someone requested this change in the past and there is no trace
- Potentially compromised accounts or system whereas the attacker is attempting Persistence , credential access & privilege escalation
- Third party vendor compromise : if your vendor had access to your systems
- Insecure remote access or permission in AD allowing an actor making this change ( insider threat or external)
Attribute detection
In Active Directory, the attribute that controls this behaviour is the userAccountControl attribute. One of the flags in this attribute is PASSWD_NOTREQD (value 0x0020), which indicates that a user can have a blank password.
PowerShell Script Detection
Import-Module ActiveDirectory
Get-ADUser -Filter 'userAccountControl -band 32' -Properties Name, DistinguishedName | Select-Object Name, DistinguishedName
Prevention Steps
- Audit and Identify Affected Accounts:
- Use PowerShell scripts or Active Directory administration tools to scan for accounts with the
PASSWD_NOTREQDflag set in theiruserAccountControlattribute. This will help you identify all affected accounts.
- Use PowerShell scripts or Active Directory administration tools to scan for accounts with the
- Review and Audit Logs using SIEM in Active Directory:
- Check security logs and audit trails for changes made to the
userAccountControlattribute. This can help identify when the changes were made and potentially by whom. Look for Event IDs related to account modifications.
- Check security logs and audit trails for changes made to the
- Interview IT Team Members:
- Speak with members of your IT team to see if anyone remembers making these changes
- Implement a Remediation Plan:
- For each identified account, enforce password requirements and ensure that a strong password is set.
- Update your organization’s policies and procedures to include strict controls and documentation requirements for making such significant changes to account properties in the future with the help of HR
- Enhance Monitoring and Alerts for this setting:
- Adjust your monitoring tools to alert on modifications to the
userAccountControlattribute or other critical security settings within AD. This can help prevent similar issues from occurring unnoticed in the future.
- Adjust your monitoring tools to alert on modifications to the
- Conduct a Security Awareness Session:
- It’s beneficial to conduct a session on security best practices for IT staff, emphasizing the risks associated with allowing blank passwords and the importance of adhering to security policies.
- Regular Audits:
- Schedule regular audits of Active Directory and other critical systems to ensure compliance with your organization’s security policies and to detect any unauthorized or insecure configurations early.
- Limit changes on this attribute or other insecure attributes
- Limit permissions using delegation or other techniques where this attribute would not be possible to modify without an enterprise admin

