Introduction
Ironscales and other platforms are already using Adaptive AI technology for advanced phishing and BEC attacks, The AI dynamically adjusts its detection mechanisms based on real-world data and user feedback, ensuring high efficacy in threat detection and prevention.
There is more .. it also trains your users!
Launching simulated phishing attacks in a controlled environment, employees learn to identify suspicious links, unexpected email requests, and other common phishing tactics. This practical experience is often more effective in changing behaviours than theoretical training alone.
Education & training
- Education is about the knowledge transfer (Awareness Training, Learning management modules)
- Training is about practising with the acquired knowledge (Phishing Simulation)
Ask The right first questions to leadership management & stakeholders
- Do we have Cybersecurity Awareness training sessions & Modules ?
- Such Training modules being updated and when by whom?
- Does everyone know the rules and what to do about Phishing, as long as how to report it safely ?
- Are policies and procedures being updated regarding cybersecurity awareness ?
- Do you have a way to measure how effective is the cybersecurity awareness ?
- How likely a security incident would be caused for a lack of knowledge about policies and procedures, like phishing attack?
- How far would it go, depending on who clicks the phishing email and enter credentials?
- Do we have risk appetite , risk management processes regarding Cybersecurity & data?
Starting to be effective with People and IT security Systems is key
People controls
- IT Acceptable policy : if you don’t have one, start one now! (BYOD policy, Reporting Phishing, ensuring to use safely work devices)
- Interest parties should regularly update training sessions & modules regarding phishing (HR, IT, Cybersecurity, Information Officer, DPO roles should be involved on the matter)
- Phishing simulations should start on regular Quarter basis in order to measure risk & test training measures
- Phishing simulations should have targets as ( 1% click , 0.5 % entering credentials )
- Phishing simulations should have separate & increased difficulty campaigns with IT & Key admin and Stakeholders
- Adhere to GDPR or Data law breach and work together with the DPO & Security Officer to report the breaches related with Phishing Security incidents
- Follow a Cybersecurity framework, make your company cyber aware.
- Review protocols of communications for Cybersecurity phishing incidents or other security incidents
- Data protection controls (has the company done any Data impact assessment ?)
- Incident Response plans for Phishing and Data breaches should be exercised by the IT team
- Access control policies should be drawn & regularly updated.
- IT and Security teams should use Frameworks as Assume Breach/ Zero trust in identity, network, data, applications & infrastructure
Technical standard effective controls ( Recommendations )
- Consider evaluating your security posture purchasing or hiring a professional pentest
- BEC Security & Training tools (Phished.io, Iron scales, Proof point, Microsoft E5, Avanan, Mime cast) can really upskill Phishing protection & Simulations, consider purchasing one.
- Implement a strong password policy
- Utilize and implement EDR Systems that can catch Phishing or Malware
- Block Extensions in email that are not required that usually are used by thread actors
- Review your Email security platform policies, SPF records, phishing alerts & possible automations and phishing play books for the IT / Security team
- Review that your Email platform (Exchange, Google .etc) has healthy security configurations
- Account take over protections review: Malicious links, Malware
- Configure or purchase a web filtering platform blocking new recently created domains
- Policies for web filtering should be reviewed and tested
- Measure with Reports the volume of malicious email and how effective your policies are
- Use conditional access policies or similar technology to block unauthorized logins
- Implement mandatory MFA policies for users
- Implement mandatory BYOD Personal devices technical policy
- Implement Patching controls and update all known applications regularly
- Implement data policies to classify data (E5)
- Implement strong DLP and encryption policies for sensitive data in your platforms
- Implement SSO in all your known apps whenever possible to adhere to cybersecurity posture
- Utilize PIM for Administrators of any Platforms whenever possible (SSO) with administrators
- Utilize tools like Identity Protection that can tackle and take over risk sign ins
- Legacy systems like Active directory should not be accessed or visible unless strictly required
- Has your identity (Azure, Active Directory) been ever assessed ? (bad permissions, wrong configurations
- Identify valuable assets or accounts that may not adhere to the security standards and try to mitigate or lower the risk of using them
- Protect and monitor Legacy systems with priority
- Ensure to tag and monitor VIP users (leadership), IT, Application admins or any other roles in your Email security solution
- Identify weak accounts and systems in order to enforce controls protecting from phishing attacks
- Implement Hardening in Devices & Servers or any others use tools like Microsoft Score
- Perform assessment on Zero trust in Network
- Software asset control (Utilize App blocker or similar to block software that is not in a whitelist)
- Monitor and Hunt indicators of Compromise (Learn from last phishing techniques and tactics)
- Test and ensure all your Applications and System backups are healthy and effective
- Ensure any keys or backups are using 2 rule man (where access can only be given by 2 people)
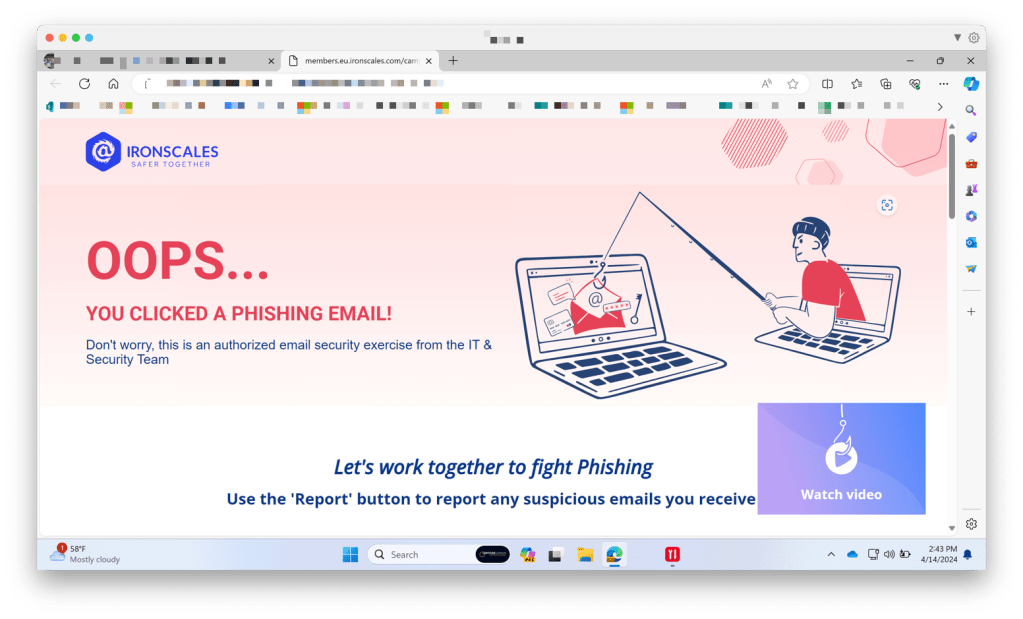
Why Is important to perform phishing simulations with tools like Ironscales ?
Automating the process : With Ironscales or other similar tools, you can easily involve more parties like your Learning and Development team or HR to help and even launch these simulations
Reducing Risk : Phishing is a common attack vector that often leads to data breaches. Launching simulations Reduces drastically the likelihood of successful phishing attacks by ensuring that employees are vigilant and knowledgeable about such BEC (business email compromise threats).
Testing and Improvement: Test the effectiveness of the current training programs and the overall security posture. The results from these tests can be used to identify areas of weakness, so do also identify current incident response plans on other departments towards breaches
Helps your ISO 27001 and other Certifications : For certifications like ISO 27001, evidence of ongoing training and incident response capability is crucial. Phishing simulations provide tangible proof that an organization is actively engaging in training its staff and improving its security practices.
Cultural Shift Towards Security: Regular training, including phishing simulations, produces a security-conscious culture within the organization. When employees are consistently reminded of security best practices, they are more likely to consider cybersecurity in their daily activities and decisions.
Related Information & Security Certifications & Frameworks that can help
- ISO 27001 Information security awareness, education & training
- NIST Framework
- GDPR: Requires that organizations train their employees on data protection practices, including phishing defence, especially if they handle personal data of EU citizens.
Iron scales Phishing simulation example ( Adobe Sign )

Iron scales AI BEC protection & Phishing Simulation module
- Ironscales has an entire module for Simulation and training to be used
- Ironscales also classifies the users on “level” based on clicks or actions
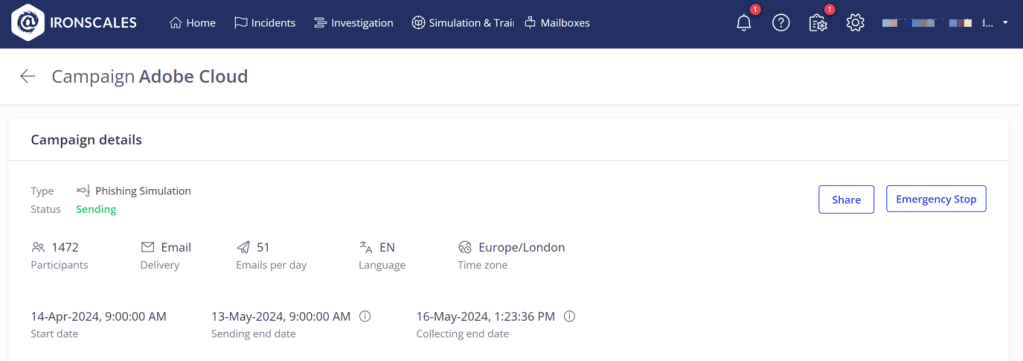
Monitor Results with Ironscales
- With Ironscales you can interact with the results and ensure you can produce KPIs based on the campaigns

Train users with Ironscales
- When colleagues click on the phishing link they are sent to specific training that iron scales can provide or you can modify with templates