- Benefits & Recommendations
- Technical requirements
- Sentinel Query – Downloads folder – Suspicious files detected
Benefits & Recommendations
- Quickly identify and respond to malware or potentially unwanted software that could compromise the security of the device or network.
- Detect unusual patterns, such as unauthorized or unusual file downloads, which may indicate the presence of a malicious insider or an advanced persistent threat (APT)
- By catching malicious files early, you can prevent attackers from gaining access to sensitive data or causing significant damage to your systems
- Combine further with extended executable queries to implement ML indicators where the “deviations can be matched”
- Block hashes of unwanted software
- Collect potential puas and upload to any.run or falcon hybrid to investigate possible malicious behaviors
Technical requirements
- Ingestion of Device endpoint logs to Sentinel
- Defender for Endpoint E5
- Sentinel instance

Sentinel Query – Downloads folder – Suspicious files detected
// The query_now parameter represents the time (in UTC) at
DeviceProcessEvents
| where FileName endswith ".exe" or FileName endswith ".docx" or FileName endswith ".msi"
or FileName endswith ".bat" or FileName endswith ".cmd" or FileName endswith ".vbs"
or FileName endswith ".ps1" or FileName endswith ".js" or FileName endswith ".scr"
or FileName endswith ".cpl" or FileName endswith ".dll" or FileName endswith ".zip"
or FileName endswith ".rar" or FileName endswith ".7z" or FileName endswith ".iso"
or FileName endswith ".img" or FileName endswith ".docm" or FileName endswith ".xlsm"
or FileName endswith ".pptm" or FileName endswith ".pdf"
or FileName matches regex @".*\.[a-zA-Z0-9]+\.(exe|scr|bat|vbs|js)$" // double extensions
| summarize count() by FileName, SHA256, FolderPath, AccountName, DeviceName, ProcessCommandLine
| where FolderPath contains "Downloads"We can observe as soon we ran the query we detect 2 executables worth looking
- PDFsam.bat ( opensource ) Batch file that can be weaponized as it runs by bat code via github
- SodapdfDesktop
- Chrome web companion addon
We can deem the possible executables as PUA ( potentiall unwanted apps) and something that would be worth monitoring
Setup web companion executable detected by the query – potentially malicious
Suspicious executable web companion , deemed malicious by any.run , report can be read further down

sodapfg- analysis with ANY run – Example alert – Malicious PUA
- Executable could be suspicious PUA

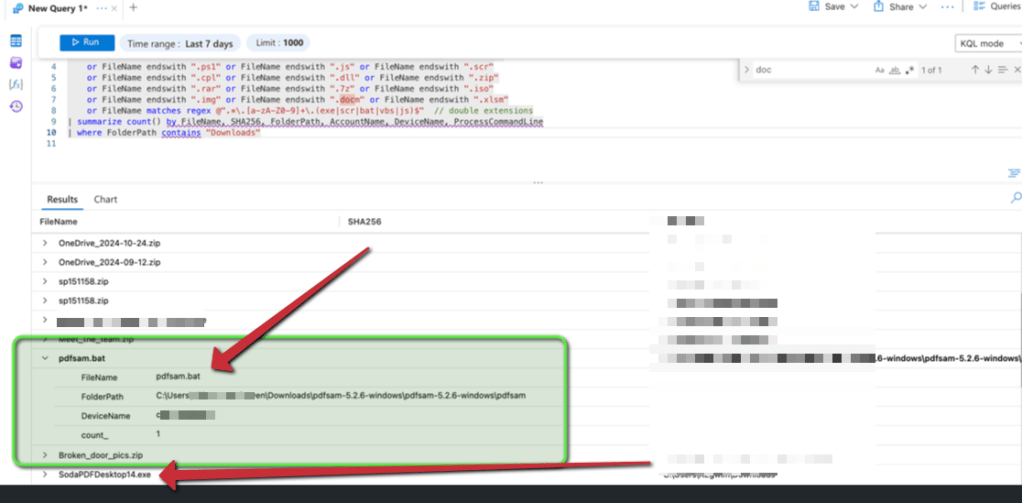
PDF sam detection – Opensource PDF batch file
The original script is harmless. It is intended to facilitate the use of PDFsam. However, any batch script can be altered to perform malicious activities.
Privilege Escalation: If the script were executed with administrative privileges, it could escalate permissions. This could allow it to perform unauthorized actions on the system.
- Adding Malicious Code: Attackers could inject commands
- Delete System Files: Use commands like
delto remove critical files. - Modify System Settings: Use
regcommands to change Windows Registry settings. - Execute Malware: Add commands to download and execute malicious files from the internet.
It is very important to maintain a logical monitoring on end users for the use of this tools & Scripts