If you ever wondered why when applying permissions on Windows Enviorment takes time to apply to the user the response is : the Kerberos ticket
The trick is simple just running the following command you should refresh the permissions without having to reboot
Open cmd.exe
run Klist purge

Now I would like to go through the Windows Actual AUTH processes and some security concerns and mitigations you should consider
Beware at the end of the article I have attached an official Microsoft PDF to mitigate pass the hash attacks
About Kerberos and NTLM
We can see some insights here on the Microsoft page and all together I’ve pulled out some info for you
https://docs.microsoft.com/en-us/windows-server/security/kerberos/kerberos-authentication-overview
The Kerberos ticket is used wide in Windows system domains , it had on the past questionable security due using DES ( data encryption standard )
Security concerns are still in the protocol as some protocols have still not been updated to other cyphers like AES
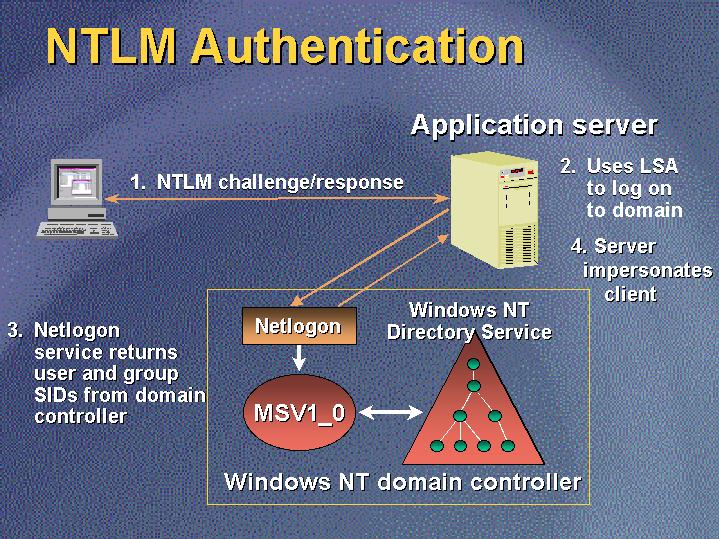
Things to consider for example in old enviorment , NTLM will always be used when a computer is not into the domain . ( ntl lan manager ) . This protocol was replaced with Kerberos in the year 2000 . NTLM was in part written by IBM and Microsoft.
Attacks Kerberos
Pass the ticket ( gaining local admin in the machine , would allow to use the ticket AUTH instead of password )
Mitigations for common Kerberos attacks
Use LAPS for local admin management
Use Tiered Adminstration
Do not allow Local admin cached logins
0 Trust Port configs in Servers –
Do not allow Domain admins to login remotely in servers , use tiered configs as a local admin for the server. If possible restrain in servers to allow Domain Admins to run commands over the network . Beware this configuration cannot always be applied. Specially in Remote desktop enviorment where the license server must be added to the group “Terminal License Servers”
Completely block domain controllers in a separated network where only with a trusted VM you can remote ( jump server ). If possible only accessible through a VPN with 2mfa .
Use AppLocker , and good antivirus defences in jump server. Shut down the servers when not being used during the day
Monitor any activity or changes in the Tiered accounts or Domain admin accounts ( use ATP , or a third party exploit anaylizer)
Do not allow the network to be opened in Wi-Fi enviorment if possible . Use always VPN
Implement 2mfa tokens for legacy authentications
Perform regular updates in clients and servers
Use Core isolation ( Windows 10 ) . Defender Guard policies
Migrate to Azure AD and if possible be a serverless company and use software as service in the cloud
Try to get away from Remote Desktop Legacy enviorment opened to the internet
If using azure Consider using Azure Bastion to remote in your servers
Update your systems regularly
Block internet outbound /Inbound when possible ( in every server )
Stay updated for security news
Limit your domain admins as much as possible
Implement access on demand
Bastion forest ( not always possible )
Change passwords regularly .
Control local admin users ( specially in servers )


Considerations of NTLM
Weak Cryptography ( hash md4)
When a client sends AUTH , there is not an implementation of a way to validate the identity of the server, wich opens up attacks of man in the middle
No multifactor ath
NTLM2 ( updated version ) has mitigated some securiy flows but as for today it is still a security issue
Attacks than can be used against NTLM
Pass the hash
Man in the middle ( relay attacks)
Mitigations against NTLM attacks
If possible you should get rid of NTLM protocols .
If that option is not on the table, make sure you update your operating systems regularly
Monitor NTLM usage ( either with scripts or third party solutions )
Enforce LDAP /SMB SINGING : https://docs.microsoft.com/en-us/troubleshoot/windows-server/identity/enable-ldap-signing-in-windows-server
Kerberos authentication flow

NTLM